What Is ARP Spoofing? Avoid ARP Poisoning Attacks
Over the years, hackers have employed various methods to carry out cyberattacks. Local area networks are frequent targets of online threats, primarily because they are the backbone of most organizational and home network environments.
Some of the most dangerous attacks involve intercepting the communication between devices on a network. Among these, ARP spoofing, meaning Address Resolution Protocol spoofing, stands out as an effective method attackers use. In this article, learn what ARP spoofing is, how it works, its dangers, and how to prevent it.
What is ARP (Address Resolution Protocol)?
To understand ARP spoofing, you first need to know what ARP does. ARP, short for Address Resolution Protocol, was defined in 1982 by RFC 826. It’s a network protocol for mapping IP addresses to physical media access control (MAC) addresses and vice versa.
Within a local area network, devices communicate using two types of addresses: IP addresses for logical addressing and MAC addresses for physical addressing.
Each device on a network maintains an ARP cache. The cache contains a list of known IP and MAC address pairs, which it references when sending data.
If a device needs to send data but does not have the MAC address of a target IP, it sends out an ARP request. This broadcast message asks, "Who has this IP address?" The device with that IP responds with its MAC address.
Once received, the sender stores this information in its ARP cache for future use. By keeping this mapping, ARP ensures quick and efficient communication between devices. Most Internet-enabled devices we use utilize Address Resolution Protocol to connect to routers or gateways for Internet access.
However, the ARP protocol isn’t designed for security. Thus, it is vulnerable to cyber threats like ARP spoofing, an attack in which false ARP messages are sent to trick devices into associating the wrong MAC address with an IP.
What is ARP spoofing?
Address Resolution Protocol (ARP) spoofing, also known as ARP poisoning, is a type of cyberattack where a malicious actor sends falsified ARP messages over a local area network (LAN). Local networks, of course, support ARP packets.
The term "ARP spoofing” often does not describe a specific attack. It encompasses a range of attacks that exploit the ARP protocol to deceive network devices into associating incorrect MAC addresses with known IP addresses. So, spoofing is a starting point for more complex network attacks such as Denial-of-Service (DoS), session hijacking, man-in-the-middle (MitM) attacks, and more.
In Address Resolution Protocol spoofing, an attacker exploits the lack of verification in ARP messages. They send false ARP replies on the network, tricking devices into updating their ARP caches with incorrect MAC addresses. Once an attacker successfully executes the attack, they can intercept, modify, or block communication between devices on a local network.
For example, if the attacker wants to impersonate the network gateway, they send spoofed ARP responses linking their own MAC address to the gateway's IP address. This results in other devices on the network sending their traffic to the attacker, believing they are communicating with the gateway.
ARP spoofing is possible because the ARP protocol lacks an authentication mechanism. Devices on a local network trust incoming ARP replies and automatically update their ARP caches, even if they did not request the information.
This vulnerability makes ARP spoofing relatively easy to execute using readily available tools, especially on Ethernet-based networks like WiFi or wired LANs.
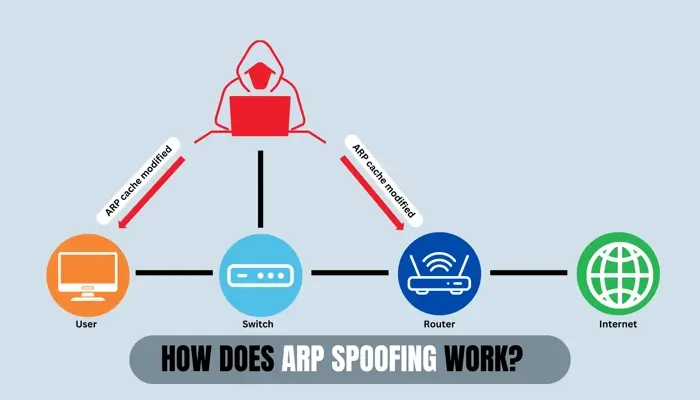
How ARP spoofing works
Attackers must associate their MAC address with the IP of a target device. By altering ARP tables, an attacker gains control over how data frames travel through the network.
The ARP poisoning attack takes advantage of the trust that devices place in ARP replies. Here's a step-by-step explanation of how it is executed:
- Preparation. The attacker scans the network to identify the IP and MAC addresses of the devices. The attacker first scans network traffic to gather vital information, including IPs and MACs of target devices. It can be the gateway and a victim device.
- Sending ARP replies. Once the attacker has the necessary information, they send falsified ARP replies to the victim's device and the gateway. These replies associate the attacker’s MAC address with the IP of the gateway on the victim's device and vice versa on the gateway.
As a result, both the victim and the gateway believe that they are communicating with each other. But in reality, they are both sending their traffic to the attacker. - Interception. Once ARP spoofing is in place, the attacker intercepts the traffic between the victim and the gateway. This allows the attacker to either passively eavesdrop on the communication, actively modify the data, or completely block it.
Suppose an attacker wants to intercept communication between a user's computer (IP: 192.168.1.5) and the network router (IP: 192.168.1.1). The attacker sends ARP spoofing messages to both the user's computer and the router:
- To the user’s computer: "192.168.1.1 is at (attacker's MAC address)."
- To the router: "192.168.1.5 is at (attacker's MAC address)."
Both the user’s computer and the router update their ARP caches with the attacker’s MAC address. Now when the user sends data to the router, it first goes to the attacker, who can monitor, modify, or drop the traffic before forwarding it.
Why ARP spoofing is possible
ARP poisoning is possible primarily due to inherent weaknesses in the ARP protocol itself. These weaknesses include a lack of verification, the dynamic nature of ARP caching, and ARP’s stateless nature.
- Lack of authentication. The ARP protocol features no mechanism to verify the authenticity of ARP messages whatsoever. When an ARP reply is received, the receiving device has no way of knowing if the message came from the actual device associated with the IP address or from an attacker. It blindly accepts ARP replies regardless of the sender's identity.
- Dynamic ARP cache. ARP is a dynamic protocol where devices update their ARP cache whenever they receive an ARP reply. It doesn’t matter if the reply was unsolicited or not. Therefore, attackers continuously send spoofed ARP messages to maintain their presence in other devices' ARP caches.
- ARP’s stateless nature. ARP is a stateless protocol. This means devices don’t track whether an ARP reply corresponds to a specific ARP request. This allows attackers to send ARP replies even when no ARP request was made.
Dangers of ARP spoofing
The consequences of a successful ARP spoofing attack can be devastating. When attackers intercept traffic, they’re likely to cause catastrophic impact.
Hackers can steal and manipulate data
Once hackers infiltrate your network, they can steal data. They redirect network traffic to their own devices so they can monitor your activity and capture sensitive information, like passwords and financial details.
Beyond theft, they can modify data, corrupt files, and disrupt communications to compromise security.
ARP poisoning can disrupt systems and halt performance
ARP poisoning can overwhelm your network with false ARP messages. In an organization, it causes devices to crash and disrupt normal operations eventually.
It may lead to slower network performance, reduced Internet speeds, delayed file transfers, and poor online experiences.
It causes damage to network infrastructure
These attacks also strain your network infrastructure. Criminals' constant flood of fake ARP requests consumes network resources, affecting not only bandwidth but also device functionality. The effects of ARP poisoning threaten your network stability.
Hackers can eavesdrop on communications
A successful ARP spoofing attack can have severe impacts on communication. The attacker can take control of how devices within a network interact with each other. The captured sensitive information is used for unauthorized access to secure systems.
Types of ARP spoofing attacks
An ARP spoofing attack causes severe damage to the targeted network. It can also be used as an opening for other attacks, such as man-in-the-middle attacks, malware incidents, and more.
Man-in-the-middle (MitM) attack
In a man-in-the-middle attack, the attacker positions themselves between two devices on a network. They intercept and monitor the communication between these devices and eavesdrop on the conversation to steal sensitive information, such as financial data.
Furthermore, they can alter the data exchanged between the devices. The communicating parties are unaware of this interference because the attacker forwards the traffic after manipulation.
Denial-of-service (DoS) attack
During denial-of-service attacks, the attacker floods the network with false ARP replies. This action overwhelms network devices, causing them to slow down.
Linking multiple IP addresses to non-existent MAC addresses, the attacker blocks communication on the network. Users can’t access essential resources with their devices.
Malware injection
With malware injection, the threat actor interferes with intercepted data packets to include malicious software. They use ARP poisoning to redirect network traffic through their device.
As users unknowingly access websites or files, the ARP spoofer injects malware into the data stream. This malware can include viruses, ransomware, or spyware.
Session hijacking
Session hijacking involves stealing session cookies used during an active session, like a website login. The attacker uses ARP spoofing to trigger the communication between a user and a server.
Getting hold of session identifiers allows unauthorized access to the user's accounts or applications. This type of attack poses serious privacy threats to personal and corporate accounts.
Techniques and tools for detecting ARP spoofing
Detecting ARP poisoning can be challenging due to its stealthy nature. These attacks go unnoticed because they manipulate the fundamental protocols that networks rely on. However, these methods and tools can help identify these threats.
Static ARP entries
Configuring static ARP entries permanently binds IP addresses to specific MAC addresses. This method prevents ARP spoofing by ensuring the IP-MAC mapping does not change, even if an attacker sends forged ARP replies.
Network administrators manually set these static entries for critical devices like routers. While effective, this technique requires constant management in more extensive networks. Adding or removing devices involves updating the static ARP table, which is always time-consuming.
Enable ARP inspection
Dynamic ARP Inspection (DAI) is a security feature on some network switches. It verifies ARP packets by comparing them against a trusted database of known MAC-IP mappings.
If an ARP reply does not match the trusted entries, the switch blocks the packet, preventing the spoofing attempt. DAI enforces strict IP-MAC address validation to protect against attacks.
Network monitoring tools
Network monitoring tools like Wireshark actively scan ARP traffic for unusual patterns. They identify anomalies, such as a device suddenly claiming multiple IP addresses. These signs often indicate ARP spoofing attempts.
Tcpdump and Wireshark are two commonly-used network monitoring tools. Tcpdump is a command-line packet sniffer that can detect ARP spoofing. Wireshark analyzes the network and sniffs the packets through the communication channel.
How to prevent ARP spoofing attacks on a network
With attackers exploiting network vulnerabilities, there are some expert-recommended ways you can mitigate ARP spoofing threats.
- Secure protocols (VPNS). Using secure protocols like HTTPS and VPNs can encrypt network traffic, making it more difficult for attackers to intercept.
- Network segmentation. Dividing the network into smaller segments can limit attackers from spreading attacks laterally.
- Implement static ARP. Setting static ARP entries binds specific IP addresses to fixed MAC addresses. This method prevents devices from processing forged ARP responses.
- Use packet filtering. Packet filtering inspects network traffic for signs of ARP poisoning. It detects and blocks malicious ARP packets before they reach the network.
- Regular spoofing tests. Conducting spoofing attack tests identifies vulnerabilities within your network. Identifying these issues promptly gives you time to fix them.
- DHCP snooping. The security feature controls the DHCP traffic within a network to ensure only legitimate devices receive IP addresses.
- Enable port security on switches. Port security restricts switch ports from recognizing only one MAC address at a time.
Frequently asked questions
What are common signs of ARP spoofing?
Slow network speeds, frequent disconnects, and duplicate IP addresses indicate spoofing.
What devices are vulnerable to ARP spoofing?
Any device that uses ARP for communication can be targeted. That’s all devices on a local network, including PCs, servers, and routers.
Is ARP spoofing limited to wired networks?
No, ARP spoofing can affect both wired and wireless local networks.

