What Is Asymmetric Encryption? Understand Asymmetric Keys
The digital age has transformed how we share information over the Internet. When you send a message, you want it to be read by the intended recipient only. This is where advanced security measures like encryption and asymmetric cryptography matter the most. In this article, learn what asymmetric encryption is, how it works, and why it's important.
What is asymmetric encryption?
Asymmetric encryption, also known as public-key encryption, is a data protection method that uses a pair of public and private keys to secure a message. The public key is used for encryption while the private is for decryption.
Asymmetric encryption emerged as a revolutionary advancement in cybersecurity. Traditional symmetric encryption systems use the same key for encryption and decryption, which poses a challenge for secure key exchange.
In 1977, Whitfield Diffie and Martin Hellman introduced the concept of public-key cryptography. They demonstrated that secure communication was possible without sharing a secret key. This breakthrough laid the foundation for modern encryption methods and protocols now integral to data security.
The main idea behind asymmetric encryption is using two distinct keys: one for encrypting and another for decrypting data. At the heart of public-key technology is the cryptographic algorithm, which uses a key generation protocol to generate a key pair.
Both keys are mathematically related. The algorithm generates them simultaneously but distinctly so that only the intended recipient can decrypt the message. Anyone can use the public key to encrypt data, but the private key is kept secret by the owner and is used to decrypt data that was encrypted with the corresponding public key.
This type of encryption allows secure communication over insecure channels. It eliminates the need to exchange secret keys, reducing the risk of interception.
Email communication is one of the many ways to show asymmetric encryption. Major protocols that rely on asymmetric encryption include the Secure Sockets Layer (SSL), Transport Layer Security (TLS), and HTTPS.
How does asymmetric encryption work?
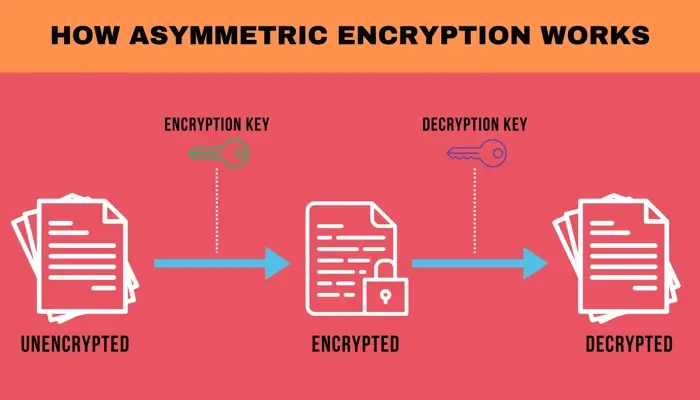
Asymmetric encryption utilizes a pair of cryptographic keys: a public key and a private key. These keys are generated together and are mathematically related but distinct.
Asymmetric encryption occurs in three steps: key generation, encryption, and decryption.
- Key generation. The process begins with generating a public-private key pair. The private key remains confidential, while others receive access to the public key.
- Encryption. When a sender wants to transmit secure information, they use the recipient's public key to encrypt the data. This transformation makes the data unreadable to outsiders.
- Decryption. Upon receiving the encrypted data, the recipient then uses their private key to decrypt the information. The private key is the only tool that can reverse the encryption process.
In an illustration, imagine you want to send a secure email to a friend. Your friend generates a public and private key pair. They share the public key with you.
You use their public key to encrypt the email and send it. Only your friend can decrypt the email using their private key.
The beauty of asymmetric encryption lies in its ability to ensure secure communication without exchanging secret keys. In environments where secure key distribution is challenging, the technology stands out.
Another selling point for asymmetric encryption is its authentication capabilities. It confirms the origin and integrity of messages through digital signatures.
The mathematical principles underlying asymmetric encryption are complex but robust. This complexity is why asymmetric encryption has become a cornerstone of modern cryptographic systems.
Types of asymmetric encryption algorithms
Asymmetric encryption algorithms are diverse; however, you may encounter a few common types. Consider these asymmetric encryption examples below.
Rivest–Shamir–Adleman (RSA)
RSA is a fundamental asymmetric encryption algorithm widely used for securing data. It relies on the mathematical challenge of factoring large prime numbers.
RSA creates public and private keys by multiplying two large primes. This results in keys that are difficult to break. However, the encryption and decryption process can be slow because of the extended key lengths, often 1024 or 2048 bits.
Diffie-Hellman Key Exchange
Diffie-Hellman facilitates secure key exchange over public networks. It uses numbers raised to certain powers to create decryption keys, ensuring that sensitive information does not transmit outright.
The algorithm enables two parties to generate a shared secret key without direct exchange. By leveraging public-key techniques, Diffie-Hellman keeps threat actors away.
Elliptic Curve Digital Signature Algorithm (ECDSA)
ECDSA, an advanced public key cryptography algorithm, uses elliptic curve cryptography to secure data. It provides the same level of security as other digital signature algorithms but with smaller keys.
The protocol’s design makes it nearly impossible to reverse the private key from the public one. Its primary applications include digital signatures and random number generation.
Pretty Good Privacy (PGP)
PGP, a recognized email encryption program designed to secure files, uses an asymmetric key encryption method to allow users to encrypt data with a public key and decrypt it with a private key. However, today, "PGP" refers to any software adhering to the OpenPGP standard.
ElGamal
ElGamal is an asymmetric cryptography algorithm based on the Diffie-Hellman key exchange. Known for flexibility and adaptability, it provides both encryption and digital signatures.
Each algorithm has specific considerations, such as key size, performance, and security. The choice of algorithm depends on the application's requirements.
Advantages and disadvantages of asymmetric encryption
Asymmetric cryptography offers several advantages to other types of encryption, but it also has a few drawbacks. Being aware of these can help organizations make informed decisions about implementing cryptographic solutions.
Advantages
Asymmetric encryption key distribution eliminates the need for secure key exchange, as the shared public key reduces the risk of key compromise. Additionally, digital signatures provide a means of verifying the authenticity of messages.
Only the intended recipient can decrypt the messages, meaning nobody has unauthorized access. The method scales well in environments where multiple users need secure communication. Each user only needs a single public-private key pair. It also provides non-repudiation, meaning the sender cannot deny sending a message.
Disadvantages
On the other hand, asymmetric key cryptography is intensive and slower than symmetric key encryption. This is a drawback in environments requiring high-speed data processing. Key management of a private key can also be challenging because it must be kept secure.
The mathematics underlying asymmetric encryption is complex, and therefore it requires more resources, which can be a limitation in devices with restrained processing power.
Use cases of asymmetric encryption
Asymmetric cryptography works in various applications and industries, providing secure communication and data protection. Here are some common use cases:
- Secure email communication. Asymmetric encryption ensures the confidentiality of email messages. Programs like PGP use public key cryptography to validate the email sender's identity.
- SSL/TLS for secure web browsing. SSL/TLS protocols use asymmetric encryption to secure data transmitted between web browsers and servers. They establish a secure connection to safeguard sensitive information like credit card details.
- Digital signatures. It enables the creation of digital signatures, which prove the integrity of not only documents but software, too. Authentication builds trust in electronic transactions.
- Blockchain and cryptocurrencies. Blockchain networks and cryptocurrencies employ asymmetric encryption for security purposes. This method secures the transfer of digital assets.
- Virtual private networks (VPNs). VPNs use asymmetric encryption to establish secure connections between remote users and corporate networks. This later protects sensitive data from tampering.
- Public Key Infrastructure (PKI). PKI systems use asymmetric encryption to manage digital certificates.
- The Internet of Things (IoT). Asymmetric encryption is a valuable tool for securing IoT devices, especially as technology continues to advance.
Difference between symmetric and asymmetric encryption
Symmetric and asymmetric encryption are two fundamental cryptographic methods. Understanding the differences between them is essential for selecting the appropriate encryption method for a given situation.
| Symmetric encryption | Asymmetric encryption | |
| Key use? | Uses a single key for both encryption and decryption, which must be kept secret and shared securely between parties. | Uses a pair of keys: a public key and a private key. The public key can be shared openly. |
| Resources | Faster and requires fewer computational resources, makes it ideal for encrypting large volumes of data. | Slower and more resource-intensive, which is why this type encrypts large volumes of data. |
| Security | The security depends on the secrecy of the key. If the key is compromised, the encrypted data becomes vulnerable. | Provides strong security guarantees with the public-private key pair, therefore ensuring that only the intended recipient can decrypt the message. |
| Key distribution | Exchanging keys over insecure channels can lead to interception. | Key distribution is more straightforward in asymmetric encryption, as the public key can be shared openly. |
| Size of keys | 128 or 256-bit key size. | RSA 2048-bit or higher key size. |
How asymmetric encryption is used in SSL/TLS certificates
SSL/TLS certificates use asymmetric and symmetric encryption to secure website data. When a user navigates to a secure website, their browser initiates a connection with the server hosting that website. The server then sends its public key to the browser to establish a secure connection.
This public key, therefore, plays a crucial role in authenticating the server's identity. Once the public key confirms the server's identity, the browser and server engage in a key exchange process. This process involves using asymmetric encryption to establish a shared secret known as a session key.
With the session key instituted, the connection transitions from asymmetric to symmetric encryption as the latter provides better speeds. This transition is because symmetric encryption is much more suitable for encrypting large amounts of data quickly.
Frequently asked questions
What is a public key?
A public key is a cryptographic key used in asymmetric cryptography. It encrypts data and the user can also share it openly with anyone.
What is a private key?
A private key is a confidential cryptographic key used in asymmetric encryption. The owner must keep it secret, however, as it decrypts data encrypted with the corresponding public key.
How are public and private keys generated?
Public and private keys are generated using mathematical algorithms to create a unique pair of keys.
What are digital signatures, and how do they relate to asymmetric encryption?
Digital signatures are cryptographic techniques that verify the authenticity of digital messages or documents. In asymmetric encryption, the sender creates a digital signature using their private key, and then the recipient verifies it with the sender's public key.

