What Is Password Hashing & How Does It Work?
Frequent data breaches in the last few years show the urgent need for stronger data protection. As technology continues to expand, so do attackers' methods. Password hashing makes it much harder for hackers to break into accounts because the passwords are scrambled in a way that’s almost impossible to reverse. In this article, learn what password hashing is, how it works, and how it protects your information.
What is password hashing?
Password hashing is a way to keep passwords safe by turning them into a scrambled code using a process called a hashing algorithm. This method makes it nearly impossible to reverse the scrambled code back into the original password, even if someone manages to steal it.
When you create or update a password, the system uses a hashing process to convert it into a unique hash, storing it in the database rather than your actual password.
Upon trying to log in, the system hashes the passcode you enter and checks if it matches the hash saved in the database. If they match, you receive granted access.
Even if hackers or dishonest insiders manage to steal the database, they only get the hash - not your actual password - and the hash lacks the functionality to log in or convert back to the original password.
A key feature of hashing is that the same passcode always creates the same hash. This consistency helps check if a password is correct, but it also means two identical passwords will have the same hash.
Some common hashing algorithms include bcrypt, Argon2, and SHA-256 (from the Secure Hash Algorithm family). These methods work by taking passwords of any length and turning them into a unique, fixed-length code.
For a long time, this was the standard way to store passwords, and many systems, like Windows, still use it. However, some older hashing methods have weaknesses. As technology improves, outdated algorithms may allow "collisions," where two different passwords create the same hash. It’s advisable to use secure algorithms to stay ahead of potential threats.
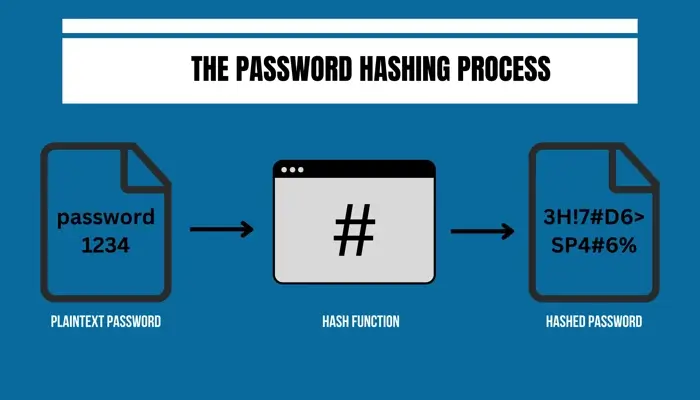
How does password hashing work?
Password hashing turns plaintext passwords into secure, scrambled codes called hashes. It makes passwords safe and hard for hackers to figure out. Here’s how it works.
- The user creates a password. When you sign up or update your password, you type it in as plaintext. This starts the hashing process.
- The system adds salt. Salt ensures that even if two people use the same passcode, their hashes will differ. This prevents hackers from using pre-made hash-cracking tools.
- The system creates the hash. Next, the system combines your password with the salt and runs it through a special hashing algorithm, like SHA-256. These algorithms apply complicated math to scramble the password and turn it into a fixed-length hash. They also take time and use a lot of computer power, making it harder for hackers to guess passwords.
- The system stores the hash. The system saves the hash and salt in the database. It stores the salt alongside the hash so the system can use it later to check if the entered password matches.
- The password is verified. When you log in, you type in your password again. The system takes the salt stored with your account, combines it with the passcode you entered, and hashes them together using the same algorithm.
If the new hash matches the stored hash, the system will know your password is correct and let you log in. The entire process works without ever storing your actual password.
Reasons to use password hashing
Improved security
Password hashing makes stored passwords much safer. Even if someone manages to steal the hashed passwords, it’s incredibly hard to figure out the original passwords, especially if a strong algorithm like bcrypt is used. Adding salts to the hash makes it even more challenging for hackers to crack them.
Meeting legal requirements
Many industries, such as GDPR, HIPAA, and PCI DSS, have strict rules about protecting user data. Password hashing helps companies follow these rules by ensuring that they handle passwords securely.
Avoiding plaintext risks
Storing passwords as plaintext is a huge security risk. If hackers break into a database with plaintext passwords, they can use all the passwords right away. Hashing stores passwords in a scrambled, unreadable format, making it much harder for anyone to misuse them.
Protection against attacks
Hashing algorithms are, by design, slow and resource-heavy, making it difficult for hackers to guess passwords using brute force. When paired with salting, hashing defends against rainbow table attacks, in which attackers utilize pre-made lists of hash values to crack passwords.
Gaining user trust
Strong security practices, like password hashing, show users that their data is a priority. This builds trust and makes people more likely to use a service that protects their privacy and security.
Common hashing algorithms
SHA-256
SHA-256 is part of the SHA-2 family of hashing algorithms created by the NSA. It produces a 256-bit hash and is used in things like SSL/TLS certificates, digital signatures, and blockchain. SHA-256 is currently considered safe as it hasn't been cracked.
Its speed makes it a good choice for applications where quick performance is needed; however, that same speed can be a downside since faster algorithms are easier to brute-force. Furthermore, the salt requires separate addition.
Bcrypt
Bcrypt is specifically designed for securing passwords. It automatically adds a salt to protect against rainbow table attacks and is intentionally slow to make brute-force attacks more difficult. It comes with built-in salting for extra security, and systems can increase the difficulty level over time as computers become more powerful.
While great for security, its speed can be a drawback in systems requiring quick password checks. However, for most applications, the delay is minor.
PBKDF2
PBKDF2 stands for Password-Based Key Derivation Function 2. It uses a pseudorandom function (like HMAC) combined with salt and runs the process repeatedly to strengthen the hash.
This hashing method is well-tested and commonly used. Users can increase the number of iterations to make it harder for hackers to crack. But high iteration counts can also slow down performance; setting it up for the right balance of security and speed can pose a challenge.
MD5
MD5 was introduced in 1991 and became one of the earliest hashing algorithms to gain popularity. It was considered highly secure at the time. However, over the years, hackers have found ways to break into it easily. While it laid the groundwork for modern hashing algorithms, hackers can crack it in seconds, making it unsafe for modern use.
Can someone crack hashed passwords?
Hashing protects passcodes, but it isn’t foolproof. Hackers can use several methods to try to crack hashed passwords. They include:
- Dictionary attacks. In a dictionary attack, hackers use special software to test common passwords. The software runs these passcodes through hashing algorithms to create hashed outputs that it compares to the hashed passwords stolen from a database. If there’s a match, the hacker can figure out the original password.
- Rainbow tables. Rainbow tables are large databases, like spreadsheets, that store pre-computed hashes for popular passwords. Hackers can compare stolen hashed passcodes to the entries in a rainbow table. Hackers can look up the corresponding original password from the table.
To protect against these techniques, many websites and apps salt passwords before hashing them. Salting adds a random value to each password before hashing so that their hashes will be different even if two users have the same password.
Salting combined with strong hashing algorithms provides an extra layer of security.
How to choose the right hash function
Selecting the right hash function for passwords is crucial for keeping passwords secure. There are several factors to keep an eye on:
- Security considerations. The primary goal of a hash function is to protect data, so its security features are critical. Choose an algorithm with no known vulnerabilities, like Argon2, specifically designed for password hashing. The hash function should also be resistant to password attacks such as brute force.
- Performance considerations. A good hash function should take enough time to make brute-force attacks harder but not so much time that it slows down the user experience. Additionally, think about scalability—if your application handles many users logging in simultaneously, you’ll want a hash function that won’t overwhelm your system.
- Future-proofing. Technology keeps advancing, so it’s wise to choose an algorithm that can adapt over time. It’s also a good idea to pick a widely used and well-supported algorithm.
How is hashing different from encryption?
| Feature | Hashing | Encryption |
| Functionality | One-way process; once hashed, data cannot be reverted to its original form. | Two-way process; data can be encrypted and later decrypted using a key. |
| Output length | Fixed length; password hasher algorithms produce a consistent output size, regardless of input size (e.g., SHA-256 creates a 256-bit hash). | Variable length. the length of encrypted data (ciphertext) depends on the input and algorithm used. |
| Primary purpose | Verifying data integrity and securely storing sensitive data like passwords. | Protecting data that needs to be accessed later, such as in secure communication and file storage. |
| Reversibility | Irreversible; original data cannot be retrieved from the hash. | Reversible; original data can be recovered using the correct decryption key. |
| Common applications | Password storage, data integrity checks | Secure communication (e.g., HTTPS), encrypted file storage, messaging |
Best practices for implementing password hashing
To keep user passwords secure, following best practices when implementing password hashing is essential. These steps help protect against attacks and ensure the system stays reliable over time.
Choosing the right hashing algorithm
Selecting a secure algorithm is one of the first steps. Algorithms like bcrypt, Argon2, or PBKDF2 work specifically for password hashing by design. They include features like salting that bans adjustable hackers from guessing passwords. Avoid outdated algorithms like MD5 because they’re no longer secure.
Updating and rotating passwords
Over time, hashing algorithms can become less secure as computing power improves. To stay ahead of potential threats, update old passwords using newer algorithms to stay ahead of potential threats.
Encourage users to change their passwords regularly, especially after a data breach.
Adding rate limiting
Another effective strategy is to implement rate limiting, which slows down repeated login attempts. By limiting how often someone can try to log in, you make it harder for hackers to use brute-force attacks to guess passwords.
Using multi-factor authentication (MFA)
Password hashing alone is not enough to fully secure accounts. Adding multi-factor authentication (MFA) provides an extra layer of security. It requires users to provide another form of verification, such as a code sent to their phone.
Performing regular security audits
Regularly review your passcode hashing implementation to identify weaknesses. Stay informed about the latest developments in cryptographic algorithms in order to update your system if better options become available.
Frequently asked questions
What is password salting?
Password salting is a security technique used to add one or more random characters to the password before it goes through the hashing algorithm. These additions ensure that the same password will produce a different hashed result each time.
Where should I store hash passwords?
Store hashed passwords in a secure, access-controlled database with encryption alongside unique salts for added protection.
What is a hashed password?
A hashed password is a secure, scrambled version of a plaintext passcode created using a one-way hashing algorithm.

