What Is Secure File Transfer Protocol (SFTP)?
Data matters more in the increasingly digital age. Because of its value, businesses put a lot of thought into how data should be protected. SFTP, or Secure File Transfer Protocol, is designed to address security concerns with sending files over the Internet. In this article, learn what SFTP is, how it works, and why it's needed.
What is SFTP?
SFTP, meaning Secure File Transfer Protocol, is a standard network protocol that enables the secure transfer of files between a client and server on a computer network. It takes the basic function of regular FTP – file transfers – but adds an extra layer of security to the process.
When files are sent over a public network, like the Internet, there is a chance of them being intercepted and read along the way. This means data is exposed to potential threats. SFTP intrinsically solves many of these limitations as it focuses on security.
The Internet Engineering Task Force (IETF) designed Secure File Transfer Protocol. It operates over the SSH (Secure Shell) protocol to encrypt data during transfer. Think of it as a virtual tunnel for your files, wrapping them for secure transfer between systems.
Beyond data encryption, the protocol secures validation of two parties involved in data transfer. File transfer over secure FTP ensures only authorized persons have access to the transferred contents.
SFTP also allows for more than file transfers. It enables users to manage files on remote servers, allowing them to perform actions like deleting, renaming, or moving files. These actions happen securely within the Secure File Transfer Protocol environment.
Another notable feature of SFTP is its ability to resume interrupted transfers. If a file transfer is disrupted, SFTP can restart it from the point of failure regardless of file size.
This combination of secure transfer, encrypted connections, and file management capabilities makes SFTP a reliable choice for transferring sensitive data that requires protection. Businesses choose the SFTP solution due to its high level of security.
A real example is in banks for shielding confidential data such as customer’s SSN. Adopting Secure File Transfer Protocol can benefit your organization in meeting data compliance requirements while reducing the risk of data breaches.
How does SFTP work?
Secure File Transfer Protocol uses a client-server model over a stable Internet connection. It creates a secure channel between a client and a server for safe file transfers. The protocol relies on SSH to establish this secure connection.
The process starts when a client initiates a connection to the server. The server listens on a designated port, port 22, for incoming connection requests. Once a client attempts to connect, the server verifies the client's identity through authentication methods. These methods include a username and password or SSH keys for more secure authentication.
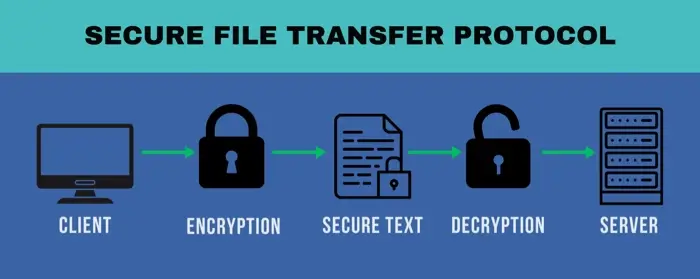
After the client is authenticated, the connection becomes encrypted. This encryption ensures that any data exchanged between the client and the server remains private. The client can now perform various file operations, such as uploading files. Each command the client sends gets processed securely because of the SSH encryption layer.
File transfers occur in small chunks of data called packets. These packets travel from the client to the server, and only those permitted can access them. Throughout the transfer, both sides maintain a secure connection.
If any issues arise, like a network interruption, the process halts without compromising security. The client disconnects from the server once the transfer or file operation is complete. The session terminates to end the secure connection.
Features of SFTP
Secure File Transfer Protocol is different from File Transfer Protocol or Trivial File Transfer Protocol, which involves even less security. The defining features of Secure File Transfer Protocol include data encryption, data compression, and login authentication, but the list below can help you understand all of the protocol's features.
Secure File Transfer Protocol:
- Encrypts the data. SFTP uses SSH encryption to protect data during transfer. Encryption turns information into unreadable code to block unauthorized access. You can transfer data within and outside your organization safely knowing your information is protected.
- Executes the command. The protocol allows users to execute commands on the remote server. Essential file operations include uploading, downloading, renaming, or deleting files on remote servers. Users gain full control over file management as a result.
- Compresses the data for transmission. SFTP secures data by encrypting it and compressing files. Compression reduces the file size. Combining security with efficiency speeds up the transfer process even over networks prone to delays.
- Authenticates login credentials. The tool requires users to authenticate with a username and password. This step aims to verify the identity of the user entering the system. Once authenticated, all data transmitted over the SFTP session is encrypted using strong data encryption algorithms like AES.
- Provides authentication to the public key. Users can authenticate using a public key instead of a password. This method is more secure and reduces the risk of password-related breaches.
All of these features contribute to a high-security protocol that protects data through transfers.
Evolution of SFTP
SFTP's evolution began with the development of the SSH protocol in the 1990s. SSH emerged as a secure alternative to Telnet and remote shell protocols, offering encrypted communication between networked devices. Developers saw the need for secure file transfers, so they extended SSH to include these capabilities. This led to the creation of Secure File Transfer Protocol.
Because of the increased number of sophisticated cyber threats, SFTP improved to meet security demands. It received upgrades like stronger encryption over time. Features like error handling followed by support for file locking and renaming were added to enhance file management.
Recently, SFTP has become a staple in enterprise environments. Its flexibility is why many businesses see it as a go-to solution for securely transferring large amounts of sensitive data between systems.
The protocol continues to incorporate new security features and enhancements. Firewalls, NAT, and proxy servers fully support it. The current version of the SFTP protocol is version 6, which works on top of SSH-2.
Earlier versions (1-5) were tied to SSH-1. Since they had security vulnerabilities, they are now considered obsolete. SFTP is a critical tool for secure file transfers despite the changes in the threat landscape.
Benefits of using Secure File Transfer Protocol
SFTP offers several advantages that make it ideal for secure file transfers. Various key benefits include the following.
Strong encryption for secure transfers
SFTP uses SSH asymmetric encryption to protect all data during transfers. As such, no one can alter sensitive information while it travels between the client and server. Unlike FTP, which sends data in plain text, SFTP ensures that both the commands and the files are encrypted.
Flexible authentication methods
Authentication is where SFTP stands out. It offers two primary methods: password-based and SSH key-based. Password authentication lets you log in with a simple username and password combination. For a higher level of security, SSH keys, and which involve creating a private-public key pair, can be used.
The server keeps the public key, while the client holds the private key. The client gets access only when both keys match.
Ensuring data integrity
Users appreciate its ability to maintain data integrity during transfer. Each data packet sent through the network undergoes verification to mitigate corruption. The process prevents damaged files from reaching their destination.
Multiple file operations in one session
You can perform multiple operations - uploading, downloading, renaming, deleting files, or even adjusting permissions - all within the same session. This versatility reduces the need for separate tools or commands.
Cross-platform compatibility
The new protocol works on almost any operating system, including Windows, Linux, and macOS. It integrates easily into existing networks without requiring either additional hardware or software. Therefore, SFTP is a practical solution for businesses with diverse IT environments.
Simplified firewall management
SFTP offers better firewall compatibility than traditional FTP. Since it uses a single port for communication, configuring firewalls becomes easier. The use of multiple ports complicates firewall configurations. This is the case with the FTP protocol.
When to use Secure File Transfer Protocol
SFTP is particularly useful when complying with security standards such as HIPAA, CCPA, or GDPR. It does help secure sensitive data while in transit.
SFTP solutions safeguard information in remote working scenarios. For example, third-party working with healthcare providers must protect electronic PHI (ePHI). SFTP enhances the integrity of this data to prevent a company from performing potential HIPAA violations.
Much like many security protocols, Secure File Transfer Protocol works well alongside VPNs to boost security. While it is a protocol for file transfers, VPNs create a secure encrypted tunnel for all data. Using SFTP within a VPN tunnel adds another defense against prying eyes.
Advantages and disadvantages of SFTP
Advantages
Businesses adopt SFTP primarily for its efficiency in file transfers and robust security features. Many implement it as part of privacy controls. Its advantages include:
- Speed. SFTP servers support large file transfers and multiple files at once. This capability saves time when moving data between servers.
- Integration. Secure File Transfer Protocol works seamlessly with firewalls. Data, commands, and sensitive information use a single connection to port 22, which firewalls enable by default.
- Manageability. Managing Secure File Transfer Protocol servers becomes straightforward with web interfaces or SFTP clients. These tools allow administrators to handle file transfers and server configurations efficiently, enhancing control over the system.
- Security. Encryption, public key authentication, and data security features ensure data integrity. These measures protect sensitive information during transfer.
Disadvantages
Although Secure File Transfer Protocol has many benefits for users and businesses, it comes with some drawbacks.
- Complexity. Implementing SFTP can be complicated for those unfamiliar with server management. Setting up SSH keys, configuring firewalls, and managing encryption add layers of technical difficulty.
- Cost. Its use may lead to higher costs due to the need for specialized servers. Again, training staff to manage SFTP systems can increase operational expenses for businesses with limited budgets.
- Compatibility issues. Not all systems or applications are fully compatible with SFTP. Old systems that don’t support this type of protocol create integration challenges.
SFTP vs. FTP: key differences
The difference between the two protocols may seem small, but it's significant. Between the two, you can entrust Secure File Transfer Protocol with your precious data.
| Feature | SFTP (Secure File Transfer Protocol) | FTP (File Transfer Protocol) |
| Encryption | Provides encryption, a method for securing data during transfer. | Does not encrypt data, making it vulnerable to outside entities. |
| Port usages | Requires only one port, port 22, to be open, so setting up a firewall is easier. | Needs multiple ports open, which complicates firewall management and increases the risk of breaches. |
| Compliance | Due to its secure file transfer process, it meets strict compliance standards, such as HIPAA, GDPR, and PCI-DSS. | Might fail to meet these standards because it lacks encryption. |
| File management | Allows for more advanced file management operations like renaming, deleting, and changing permissions. | Primarily focuses on basic file transfer operations. |
| Data protection | Ideal for transferring confidential files. | Less suitable for sensitive data transfers. |
Frequently asked questions
What is the everyday use case for SFTP in enterprises?
Enterprises automate the transmission of files to and from cloud storage services using SFTP.
Which layer does the SFTP protocol live in the OSI model?
It operates at the application layer, or layer 7 of the OSI model. This layer is responsible for providing network services directly to end-user applications.
Does Secure File Transfer Protocol support the resume of interrupted transfers?
Yes, if a file transfer gets interrupted due to network issues or system crashes, SFTP allows you to resume the transfer from the point of interruption.
What is the Secure File Transfer Protocol port number?
The common SFTP port is port 22.
What operating system uses SFTP?
Windows, Linux, and MacOS systems all support or use Secure File Transfer Protocol.

