What Is Symmetric Encryption? Learn Symmetric Key Encryption
Data protection has never been more important than today. Encryption techniques help us ensure that our data and messages are secure. There are two primary types of encryption: symmetric encryption and asymmetric encryption. In this article, learn what symmetric encryption is, how it works, and how it's used.
What is symmetric encryption?
Symmetric encryption is a data protection method that uses the same key to encrypt and decrypt an electronic message. The involved parties need to have that key, passphrase, or password so they can use it to decrypt or encrypt any messages they want.
That key must remain secret so that no other person can encrypt the ciphertext. For that reason, symmetric encryption is sometimes known as the “secret key” algorithm. Symmetric encryption matters when encryption speed is essential; for example, it's necessary for calls and correspondence in messages.
The simplest ciphers directly substitute some characters for others. They use a table, which, in this case, becomes the key. However, such ciphers tend to be somewhat easy for criminals to crack through a frequency analysis of the characters. The Caesar Cipher is a good example.
Symmetric key ciphers appeal to many organizations because they are cheap despite the level of protection they afford.
Modern symmetric encryption algorithms alternate character substitution with permutation, which is reordering parts of the message for reliability purposes. The key typically receives encryption before sending it, this time using asymmetric cryptography.
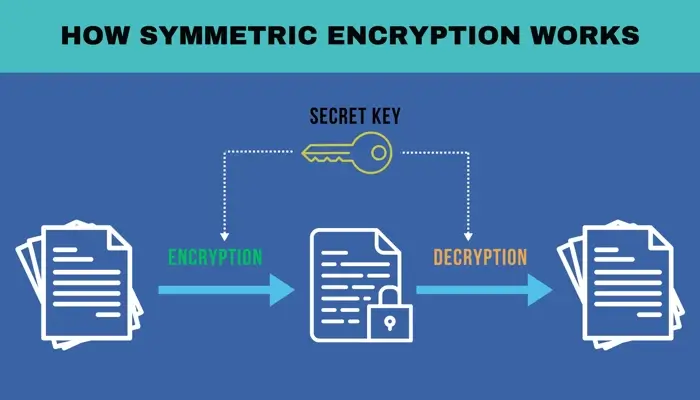
How symmetric key cryptography works
Generally, symmetric encryption works by converting plaintext into ciphertext and vice versa using the same key that is computationally infeasible to crack.
Here's a detailed breakdown of the process.
Step 1: Key generation
The key is generated using cryptographic algorithms that rely on complex mathematical equations. Standard key sizes include a block size of 128, 192, or 256 bits. Although you might not realize it, the size of the key plays a significant role in the security of the encryption.
Larger keys provide stronger security but may require more computational resources. They are shared between the sender and the receiver through secure channels to prevent interception.
Step 2: Encryption
The encryption process involves transforming the original data (plaintext) into an encoded format (ciphertext) using the generated key. The data becomes unreadable to anyone who doesn't possess the key.
Random data (called entropy) is added during this process to make the encryption even more secure. Even if the same message is encrypted multiple times, the resulting cipher text will look different each time.
Step 3: Transmission
With your message now encrypted into ciphertext, you can safely send it to your friend. Even if someone intercepts the message, they won't be able to read it without the secret key.
Step 4: Decryption
Once the recipient receives the ciphertext, they need to convert it back into readable plaintext using the same key used for encryption. The recipient must have access to the original secret key.
In summary, symmetric encryption involves generating a secret key, using it to encrypt a message into cipher text, securely transmitting the cipher text, and then using the same key to decrypt it back into the original message.
Types of symmetric encryption algorithms
Symmetric encryption algorithms can be broadly categorized into two main types: stream ciphers and block ciphers.
Stream ciphers
The encryption process in a stream cipher begins with generating a pseudo-random keystream. This keystream is created using the encryption key and a unique, randomly generated number known as the nonce. The result is a random stream of bits that matches the length of the plaintext.
Next, the plaintext is broken down into single bits. Each bit of plaintext is then combined with the corresponding bit of the keystream using XOR bitwise operations. This gradually converts the plaintext into ciphertext.
The recipient generates the same keystream used during encryption to decrypt the ciphertext. This process recovers the original plaintext bit by bit.
Some stream cipher algorithms include:
- RC4 (Rivest Cipher 4): Historically used in protocols like WEP and SSL/TLS.A, RC4 is reputable for its simplicity. However, many consider it insecure due to vulnerabilities that can lead to predictable keystreams.
- ChaCha20: ChaCha20 is a modern stream cipher designed to be fast and used in applications like virtual private networks and secure communications. It offers strong performance and resistance to known cryptographic attacks.
- Salsa20: It has an elegant design similar to ChaCha20. The cipher has respect thanks to its versatility in blocking other cryptographic protocols.
Block ciphers
In a block cipher, the plaintext divides into fixed-size blocks, and each block receives encryption using a cryptographic key.
The output is a sequence of encrypted blocks arranged in a specific order. The encrypted data goes to the receiver, who uses the same cryptographic key to decrypt it and return it to the original plaintext message.
The standard block cipher algorithms are AES, DES, 3DES, Blowfish, RC5 and RC6.
- Advanced Encryption Standard (AES) primarily secures sensitive data and supports key sizes of 128, 192, and 256 bits.
- Data Encryption Standard (DES) is an older encryption standard that uses a 56-bit key. Due to its short key length, it is insecure today.
- 3DES (Triple DES) is an enhancement of DES that applies the DES algorithm three times to each data block to increase security.
- Blowfish includes variable key lengths from 32 to 448 bits. The algorithm ticks the boxes when speed and effectiveness are priorities.
- RC5 and RC6 are part of the Rivest Cipher family. These algorithms are flexible and efficient.
Stream ciphers are particularly useful in software. Block ciphers, on the other hand, work better for hardware implementations due to their predictable processing patterns. They handle large volumes of data in parallel as well.
Uses for symmetric encryption
Despite being an older form of safeguarding information, day-to-day activities all over the Internet still deploy symmetric key encryption algorithms. They are used for:
Payment applications
Online banking and payment systems use symmetric encryption to verify personal identification numbers (PINs) of customers before proceeding with any transaction. For example, when you purchase online using a banking app, symmetric encryption verifies your identity using symmetric key algorithms.
Securing data at rest
Organizations store vast amounts of data, including sensitive information about users, clients, and internal operations. Symmetric ciphers secure this data at rest—meaning data stored on hard drives, databases, or cloud storage devices. It’s one of the smartest ways of preventing unauthorized access from both internal and external threats, such as disgruntled employees.
Authenticity verification
In many communication systems, verifying the authenticity of messages is paramount. Symmetric key cryptography achieves this through techniques like Message Authentication Codes (MACs) and Keyed-Hash Message Authentication Codes (HMACs). The U.S. government encrypts classified information using symmetric passwords.
SSL/TLS handshake
SSL/TLS protocols rely heavily on symmetric encryption to secure Internet communications. During an SSL/TLS handshake, symmetric encryption establishes a safe connection between a client, like a web browser, and a server, like a website. The handshake process involves verifying the authenticity of the server through certificates.
File and disk encryption
File and disk encryption are essential for protecting sensitive data stored on portable storage devices. Tools like BitLocker on Windows and FileVault on Mac use symmetric keys to encrypt entire disk drives. When the computer boots up, you receive a prompt to enter a password to decrypt the drive’s contents.
VPN networks
Virtual private networks use encryption because they need to create a secure tunnel between the user's device and the VPN server. Symmetric key cryptography is for this purpose due to its speed. Many VPN protocols like OpenVPN and IPSec use symmetric encryption algorithms like AES to encrypt data.
Advantages and disadvantages of symmetric encryption
The symmetric algorithm comes with a set of significant advantages, but at the same time, it's not perfect. Consider the advantages and disadvantages of this type of cryptography below.
Advantages
The advantages of symmetric encryption are:
- It prevents eavesdropping. One of the primary goals of a VPN is to prevent eavesdropping. Data remains unreadable without the correct key, even if someone intercepts packets during transmission.
- IoT security. IoT devices use symmetric encryption to protect data transmitted between devices and central servers.
- Speed and efficiency. This method is ideal for encrypting large amounts of data in no time because it is faster than other encryption forms.
- Security. Symmetric encryption can be extremely secure when implemented with a strong algorithm like AES and a sufficiently long key, like 256 bits.
- Simplicity. The single-key approach simplifies the cryptography process regarding implementation, execution, and management.
- Resource efficiency. Symmetric encryption is less resource-intensive and it requires fewer computational resources.
Disadvantages
On the other hand, there are several disadvantages to this type of cryptography to take into account.
- Key exhaustion. Symmetric encryption is prone to key leakage. If someone exposes any part of the secret key, it can compromise the entire encryption system.
- Lack of attribution data. Symmetric encryption does not support metadata. In other words, it cannot record information such as who accessed the data and when.
- Key management at large scale. While managing a few keys manually is feasible, it becomes impractical as the number of keys increases. In large-scale applications, manually tracking secret keys can be error-prone.
Businesses use symmetric encryption to purposely ensure the confidentiality of data stored on their servers. But the method isn't perfect. For the key to be with both entities, it must first be transmitted. This creates a loophole for an attacker to spoof the message if they manage to intercept the key on the way.
Still another drawback is that the keys to this encryption method live on forever. This means that organizations must invest in systems and processes to securely manage symmetric keys' lifecycle.
If an encryption symmetric key is lost and there is no backup, the encrypted data can no longer be decrypted, given that the same key is used for both encryption and decryption. Instead, organizations must decrypt the data and then re-encrypt it with a new key.
Losing a symmetric key can result in significant business costs. Businesses must pay attention to the process of exchanging the secret keys between parties. One approach is a custodial system in which custodians obtain portions of the key from a hardware security module (HSM).
Are symmetric keys secure?
Symmetric key security relies on key length, randomness, and the difficulty of reversing the process. While cybercriminals may understand the math, decrypting a key is impractical due to the immense time required, even for supercomputers. The complexity of deconstructing shared values makes symmetric keys highly secure against attacks.
Some of the best practices when using symmetric encryption are as follows:
- Use strong, standard algorithms like AES.
- Select adequate key lengths like 256-bit keys for AES, to suit your security needs.
- Generate random keys using a cryptographically secure pseudo-random number generator (CSPRNG).
- For message authentication, prefer HMAC (Hash-based Message Authentication Code) over older methods like cipher block chaining.
- Combine with asymmetric encryption for key exchange.
- Don’t reuse the same key for multiple purposes. Each key should be unique and unrelated to others because this prevents cross-contamination of security.
Following these practices will ensure, to the best of your abilities, the security of your symmetric keys.
Frequently asked questions
What should be the length of symmetric keys?
Use 128, 192, or 256-bit keys for strong symmetric encryption.
Which is more secure, asymmetric encryption or symmetric encryption?
Asymmetric encryption is generally more secure because it uses two different keys for encryption and decryption.
How is symmetric encryption used in cloud storage?
Symmetric encryption protects data at rest in cloud storage by scrambling data with a secret key.
What is an example of symmetric key encryption?
AES (Advanced Encryption Standard) is a symmetric encryption example.

